Introduction
Defending computer networks is not only becoming more challenging but also more paramount. Unfortunately, with coerced user interaction, network misconfigurations, and previously unknown vulnerabilities, it is only a matter of time before even the most secure network is compromised. How organizations detect and react to intrusions is critical in stopping an adversary from achieving their goals. Threat hunting leverages intelligence to proactively look for malicious cyber actors on a network
“The United States faces persistent and increasingly sophisticated malicious cyber campaigns that threaten the public sector, the private sector, and ultimately the American people’s security and privacy.” While this executive order is from present day (2021), the threat of attack by Malicious Cyber Actors (MCAs) is not new but rather evolving and increasing.
Cyber Threat Hunting Defined
Through threat hunting and incident response, hackers can be thwarted from achieving their goals during an active compromise. Threat hunting leverages intelligence to proactively seek and find MCAs on a network, whereas incident response seeks to scope, contain, and eliminate an identified MCA. Therefore, successful threat hunting triggers incident response actions.
Cyber Threat Hunting Methodology
Introduction to Cyber Threat Hunting Methodology
When hackers attack a network, they employ tools and infrastructure to conduct their operation. The attacker’s malicious files and infrastructure can be used against them to generate what are known as Indicators of Compromise (IOCs), which predominantly include hash values, Internet Protocol (IP) addresses, and domain names. In addition to IOCs, an attacker will utilize specific Tactics, Techniques, and Procedures (TTPs) to achieve their goals. Knowing how specific Advanced Persistent Threats (APTs) utilize TTPs enables threat hunting teams to detect and prevent adversaries from achieving their goals. To describe effective methodologies to hunt APTs using IOCs and TTPs, MITRE released a white paper in March of 2019. While not mutually exclusive, the threat hunting techniques teams can employ, as described by MITRE, are signature-based, TTP-based, and anomaly-based.
Signature-based Hunting
Signature-based hunting uses known, malicious IOCs to hunt on a network. Signatured-based hunting can be effective and reward hunters with quick easy victories if their operation is intelligence-driven, enhanced with IOCs for specific actors targeting the network, and the IOCs are recent and accurately reflect the actor’s tools and infrastructure. David Bianco of FireEye created what is known as the “Pyramid of Pain”, which explains the amount of resources an attacker must expend to change their indicators and not be detected in the future. While signature-based hunting can be a quick and easy detection method of an adversary, the IOCs themselves are ephemeral and cause the least amount of pain to an attacker. The Pyramid of Pain, Figure 1, shows that it is trivial for attackers to change hashes of their tools and relatively easy for them to change the IP or domain name of their infrastructure. Furthermore, IOCs can only be used to detect known attacks and will therefore fail to discover new or modified threats.
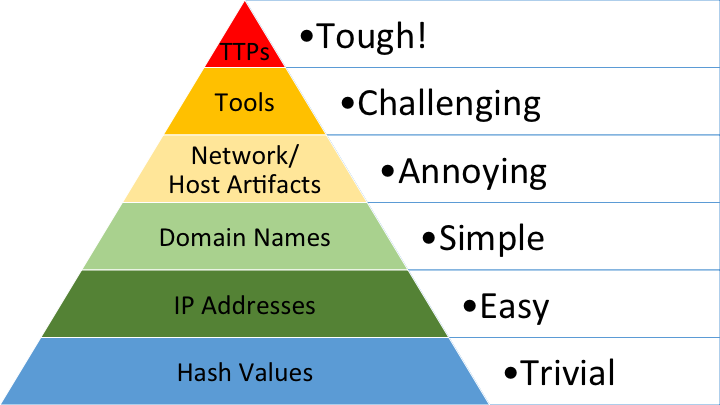
Figure 1: Pyramid of Pain
Network / Host Artifacts include anything the attacker leaves behind in their attack. Network artifacts include any network traffic an attacker sends that is distinguishable as malicious activity. This can include Uniform Resource Identifiers (URIs), distinct User-Agent Strings, or encapsulated Command and Control (C2) traffic. URIs are specific resources requested on the Internet whereas User-Agents are the program/browser to request the resource.
Host artifacts include files, directories, registry modifications. The penultimate layer, tools, refers to software the attacker brings with them in order to accomplish their goals post-compromise. Attackers can and have modified a tool they use in order to change its hash. However, if the tool’s overall functionality remains the same, then threat hunters will still be able to detect it and stop the attack.
TTP-based Hunting
The second methodology for conducting threat hunting MITRE describes is TTP-based. At the peak of the Pyramid of Pain rests TTPs. These are the most challenging indicators for an attacker to change because it encompasses their habits, training, and way of thinking. How they accomplish their overarching goal using different TTPs every step of the way. TTPs are not tool specific but rather focus on what an attacker does and how they do it. “Tactics are a high-level description of a behavior,” techniques provide a more in-depth description of the tactic, and the procedure is a low-level and very detailed implementation of the technique, often the command syntax itself.
Anomaly-based Hunting
Finally, anomaly-based detection uses machine learning and baselining to learn what is normal behavior on a network in order to detect abnormal behavior. Unfortunately, this detection requires a large amount of time and computing resources to configure and process data. Additionally, if any significant changes are made to the network, then the baseline must be reaccomplished. Even with a baseline, anomaly-based detection can produce a large number of false positives. A positive aspect of this detection method is that it can detect previously unknown attacks. For this benefit, despite its obstacles, anomaly-based detection is a useful augmentation to the other threat hunting methodologies.
Conclusion
In conclusion, cyber threat hunting is a critical aspect of network defense and companies should actively employ it. Cybersecurity will only grow in importance in the coming years with harsh repercussions for organizations that fail to adapt and implement an effective defense strategy.

